YubiKey Hardware

What is a YubiKey?
A YubiKey is a multi-protocol multi-factor hardware authenticator, providing strong authentication to a wide range of services and situations. While YubiKeys come in a number of different form-factors, each is built around the same core chipset and firmware, allowing a uniform experience regardless of the model used.
YubiKey form factors
YubiKey 5 USB-A |
YubiKey 5 NFC |
YubiKey 5 Nano |
YubiKey 5C |
YubiKey 5C NFC |
YubiKey 5C Nano |
YubiKey 5Ci |

|

|

|

|

|

|

|
USB-A |
USB-A / NFC |
USB-A |
USB-C |
USB-C / NFC |
USB-C |
Lightning / USB-C |
YubiKeys can connect to computers via a direct physical connection (USB-A, USB-C or the Apple Lightning port) or, for some models, via Near Field Communication (NFC). Regardless of how the device is connected to another machine, the interactions of all of the functions remain the same.
For details specific to each device series, refer to the Yubico Technical Manuals for each device.
Each YubiKey has a unique serial number identifying the specific device. The serial number is printed on the YubiKey’s body (both as a number as well as a 2D barcode for some models), as well as being accessible by a number of different functions by a connected computer. Regardless of how the serial number is read, it will remain the same, allowing for a uniform method of inventory tracking in both the physical and cyber spaces.
How does a YubiKey work?
When connected to another computer, the YubiKey identifies itself as a composite USB device, depending on the number of functions active. When connected physically, the YubiKey will have a different identifier depending on its current state. These Product ID and iProduct values are listed in the document, YubiKey USB ID Values guide.
When communicating with a PC or mobile platform, the YubiKey will identify itself as three devices: either a USB HID Keyboard (direct physical connection) or passive NFC NDEF Tag (NFC only); a CCID reader with a smart card inserted; and a HID FIDO Authenticator. Communication for various functions on the YubiKey will use one of the three channels.
The HID Keyboard interface passes output from the YubiKey to the host system as keystrokes from a virtual keyboard, and can use the HID Keyboard channel to communicate back to the YubiKey. For NFC interactions, this is replaced using the NFC Data Exchange Format (NDEF) tag to pass data to the host device. The CCID interface uses the standard smart card transport and Application Protocol Data Units (APDUs) to interact with the YubiKey. Finally, the HID FIDO communication allows for FIDO Client to Authenticator Protocols (CTAP1/2) to communicate with the YubiKey for U2F or WebAuthn Authentication.
Every YubiKey has a gold contact which allows for a physical touch to be utilized. This allows functions on the YubiKey to require an actual human to trigger them, protecting against software attacks attempting to hijack the functions of the YubiKey remotely. When using NFC, the act of tapping a YubiKey against an NFC reader provides the same function.
To provide direct feedback to users, every YubiKey has an LED which will light up when the YubiKey is being communicated with, or will flash when the YubiKey requires user action.
What can a YubiKey do?
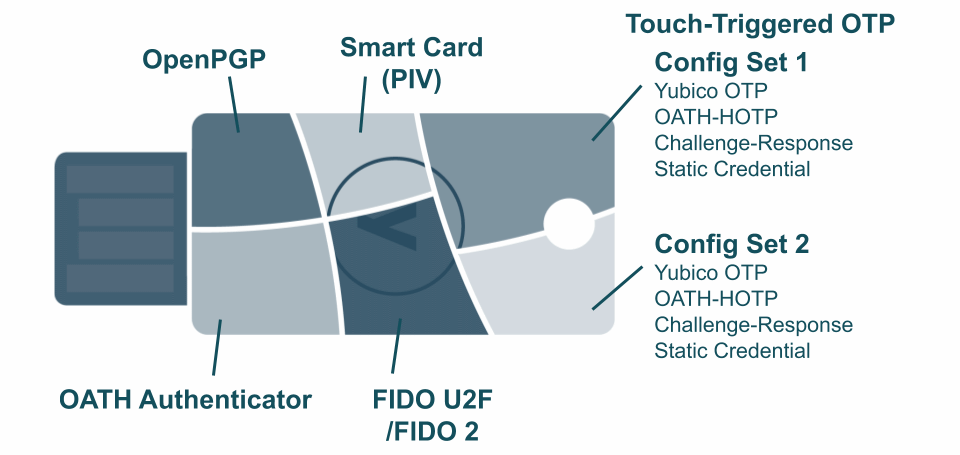
The YubiKey has five functions which support all of the authentication protocols supported by the YubiKey, with an internal management function for managing the YubiKey itself. These functions are referred to as Applications, and include:
On the YubiKey, each Application has a dedicated memory space within the secure cryptographic element, and no Application can access data stored in any of the others. For more details on what data can be stored in the YubiKey, refer to YubiKey User-Loaded Data.
The YubiKey Management Application provides the serial number and YubiKey firmware version to the other Applications, as well as being able to turn on or off access to the other functions over the physical port or NFC communication channels. Further, the YubiKey Management Application can be secured with a 16 byte lock code, preventing unauthorized modification to the YubiKey.